Helping you comply with the Digital Operational Resilience Act (DORA), a mandatory cybersecurity regulation for financial organizations, now becomes a critical part of FinTech software development and maintenance.

You must be DORA-ready in January 2025 and ensure that so are your business partners and critical service suppliers. Let’s dive deep into details and analyze how the need for DORA compliance can affect your tech processes and what important aspects you should keep in mind to meet its stringent requirements.
1 What Is DORA compliance?
DORA (Digital Operational Resilience Act) is a regulatory framework established by the European Union to enhance the resilience to operational disruptions of its financial organizations, such as banks, investment and insurance companies, credit rating bureaus, and others.
Also, the DORA framework harmonizes the rules already in place in the EU member states by eliminating gaps, overlaps, and conflicts between disparate regulations.
DORA has come a long way from a FinTech action plan first proposed in 2018 to a mandatory framework adopted in November 2022 and entered into force on January 16, 2023.
After DORA’s successful passage, a two-year transition period was started with a deadline of January 17, 2025, when financial organizations across the EU must reach compliance or face legal action if failing to comply.
2 Purpose of DORA Regulation
The two key goals of DORA include:
- addressing challenges of information and communication technology (ICT) risk management, and
- enhancing and harmonizing single regulations as those become insufficient or difficult to implement.
DORA’s implementation aims to overcome the following challenges:
- shifting focus from holding capital for covering operational risks to investing in ICT and security risk identification and management
- establishing unified technical standards and providing general guidelines that apply to different financial organizations equally
- improving navigation across regulations by removing gaps and contradictions
To Whom Does DORA Apply?
DORA is required for all financial organizations operating in the EU, both traditional and newly emerged. The key types of financial entities include:

- credit and payment institutions
- electronic money institutions
- account information service providers
- investment companies
- alternative investment funds
- management companies
- credit rating agencies
- security depositories
- insurance and reinsurance companies
- retirement funds
- trading venues and repositories
- crypto-asset service providers
- crowdfunding service providers
More importantly, DORA also applies to ICT providers. Their designation will be based on several factors. In contrast, significant factors will include the systemic impact of a provider’s failure on a financial entity’s resilience and the systemic importance of such an economic entity.
Penalties for DORA Non-Compliance
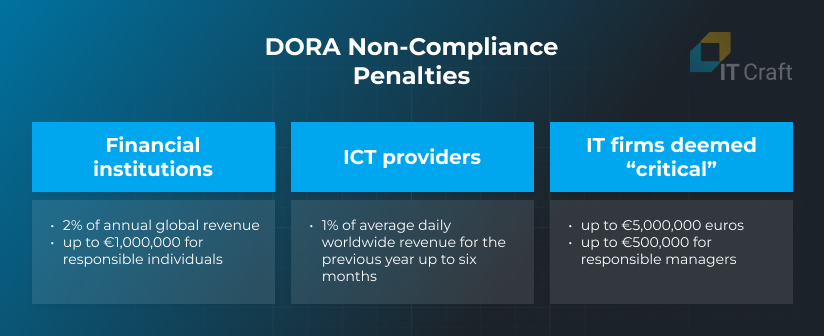
For financial institutions: imposed fines can reach up to 2% of their annual global revenues. Individuals responsible for breaches within the financial entity can face a fine of up to 1,000,000 euros.
For ICT providers: competent authorities can fine them 1% of their average daily worldwide revenue in the previous year, which they can fine every day for up to six months until the provider meets compliance.
For IT firms deemed “critical”: systemic IT companies could end up paying fines of up to 5,000,000 euros, while individual responsible managers could be imposed fines of up to 500,000 euros.
Moreover, each member state can decide on specific penalties for failing to meet DORA compliance. In some cases, criminal penalties can also be possible when those are subject under a member state’s national law. Competent authorities should receive the necessary powers and cooperate with other authorities on the case.
How Does DORA Affect Financial Organizations?
Significantly.
Financial organizations will need to reconsider all aspects of their operations: processes, people, and technologies to ensure successful DORA compliance, risk management, and effective withstanding/recovery from incidents.
The scope of required changes can be high as your organization must establish and implement comprehensive risk and incident management policies. It must also assess service providers and their DORA compliance and amend contractual closes related to security measures.
On a better note, DORA provides an opportunity to introduce long-awaited process enhancements and increase your business’s overall reliability, which can help you win customers’ trust and a different market position in a highly competitive business environment.
3 Key DORA Compliance Requirements
DORA compliance requirements help financial organizations prepare for unforeseen challenges while ensuring that their business partners and suppliers adhere to high security standards, too. It covers six essential areas, encouraging organizations to audit, manage, and increase their risk tolerance proactively:
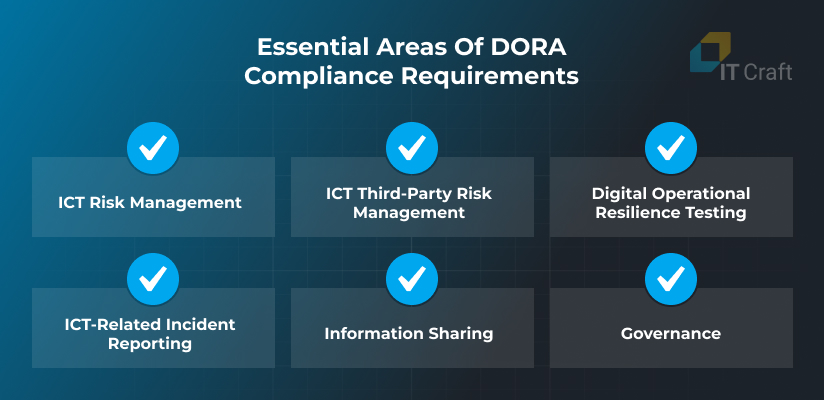
ICT risk management
Financial organizations must create comprehensive frameworks for risk management. Those can be different for various entities based on their size, nature, process complexity, and facing risks.
They must develop, document, and implement ICT security procedures covering specific technical aspects across all software lifecycle stages. Organizations must also audit processes and procedures regularly.
ICT third-party risk management
Financial organizations’ management becomes responsible for risks associated with third-party service providers that support critical functions. They must create a policy on assessing and managing a suitable service provider and cover specific compliance requirements in a contract agreement.
Digital operational resilience testing
Financial organizations must evaluate their security strength and identify vulnerabilities. They must conduct scenario-based security and penetration testing once a year and require ICT providers to participate in such testing.
Financial instructions critical for the EU financial system will also have to complete threat-led penetration testing every three years.
ICT-related incident reporting
DORA provides incident reporting requirements, obliging financial organizations to notify competent authorities of major security incidents. Also, organizations may need to notify affected clients and partners, ensuring that the provided information covers all relevant details.
Information sharing
DORA also sets a framework for volunteering knowledge and intelligence sharing on cyber threats and incidents, which helps organizations learn from each other experiences.
Governance
Financial organizations must assign ICT management responsibilities to senior managers and executive leaders who become accountable for risk management strategies and their execution.
Also, organizations must establish an oversight framework for third-party ICT providers and monitor their compliance.
4 DORA Compliance: A Checklist
The following points on your DORA compliance checklist can help you increase the resilience of your digital system and meet the DORA regulation successfully:

Understanding Scope and Requirements
DORA standards foresee certain flexibility, and financial organizations can use already existing policies, tools, documents, and procedures to eliminate double work.
Moreover, ICT security procedures are required only for essential elements. This is why the scope of work financial organizations must complete may vary based on their impact on the financial system, software size and complexity, user data, available contractual agreements with third-party IT service providers, and security practices already in place.
Gap Identification and Risk Assessment
Gaps can be assessed and documented as part of the system audit alongside scope and requirements estimate.
An organization must examine different aspects of software and infrastructure implementation and focus on the risk-based approach to such elements as:
- system capacity,
- performance management,
- vulnerability and patch management,
- data and infrastructure security,
- authentication,
- and logging.
Also, organizations must include encryption and cryptographic controls in policy while regularly auditing and enhancing cryptographic technology to ensure system resilience against cyberattacks.
Roles and Responsibilities
Similar to other security regulations and frameworks, DORA requires the top management to assign responsibilities for all ICT-related functions to an accountable person at the executive level, preferably a C-level individual.
Although specific skills and expertise are required from responsible authorities rather than the staff working at a financial organization, financial organizations need to initiate security training for their personnel to ensure employees know how to ensure operational resilience.
Remediation Plan
The responsible team needs to develop a remediation plan, including:
- identified shortcomings
- a prioritized list of remediation measures
- a root cause analysis
- staff and functions accountable for implementing remediation measures
- risks associated with failing to implement those measures and risks associated with their implementation where applicable
The team can also incorporate the remediation plan into the existing digital transformation roadmap to eliminate unnecessary planning complexity.
Assessment of Critical Third-Party Providers
Financial organizations must assess third-party providers based on their impact on:
- stability and quality of provided services,
- reliance on those providers in relation to critical functions,
- and the ease of a provider’s substitution
The critical service providers become subject to overseeing and must adopt DORA.
Moreover, financial organizations must review software packages they integrate and third-party source code on vulnerabilities and security threats when those are critical for secure, uninterrupted operations.
Threat-Led Penetration Testing (TLPT)
Threat-led penetration testing (TLPT) can be large in scope and requires checking the entire organization against contemporary cyber threats, taking technical aspects, procedures, and people into account.
On the bright side, testing should be proportionate to the size, business, and risks; an internal testing team can complete it. Only certain institutions will be required to contract third-party testers for TLPT once every three years.
Incident Response Plan
Organizations must establish processes for detecting, recording, and managing incidents and cyber threats in an incident response plan, including:
- early warning indicators,
- procedures for identifying, tracking, logging, and categorizing incidents,
- roles and responsibilities depending on different scenarios,
- notifications to staff, stakeholders, customers, and counterparts,
- reports to senior managers and authorities, and
- response procedures to mitigate the impact of major incidents.
ICT Monitoring
Ongoing ICT monitoring is required to timely detect security risks, such as:
- cyber threats and attacks,
- vulnerabilities in system source code,
- any major changes in network and system infrastructure,
- mapping interdependencies between different information and ICT assets and associated risks.
Need help with setting up and testing an infrastructure monitoring system?
Let’s assess your concerns and requirements, and see how we can help you increase your infrastructure resilience.
Contact Us
Documentation
Financial organizations must classify and document all security-related aspects, such as:
- security policies and arrangements,
- business functions, roles, and responsibilities,
- information and ICT assets that support business functions, roles, and responsibilities,
- ICT risks and mitigation measures,
- security management processes and procedures,
- third-party dependencies and their criticality,
- results of tests and system audits,
- other essential information.
Organizations must regularly update documents as part of compliance requirements.
Information Sharing
Financial organizations can participate in information-sharing initiatives to prepare for emerging threats and access the industry’s best practices. At the same time, organizations need to meet existing frameworks and regulations while participating, e.g., depersonalize any data before sharing to ensure GDPR compliance.
5 DORA Implementation Steps
Now, let’s divide the DORA compliance checklist into implementation steps:
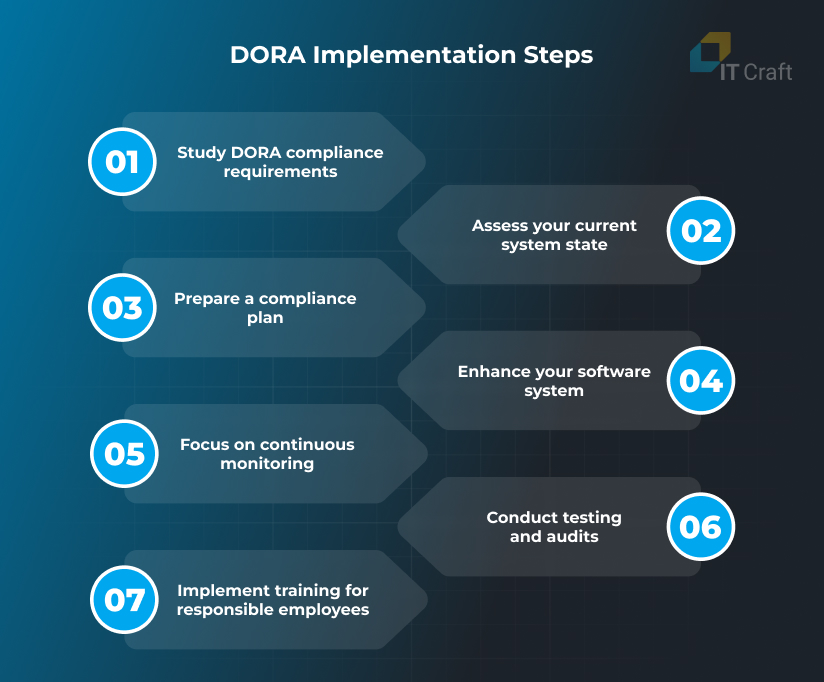
Study DORA compliance requirements
You need to review DORA compliance requirements and accompanying guidelines to determine which articles and standards apply to your system and to what extent. At this step, you should assign roles and responsibilities and ensure transparent communication between participants.
Assess your current system state
The compliance team needs to understand what security measures and policies are already implemented on the project, dividing the available scope into three categories:
- reuse for DORA compliance without changes,
- enhance available measures/policies,
- design/redesign from scratch.
Prepare a compliance plan
You must document all details of your implementation plan, including:
- responsible managers,
- required policies, procedures, and actions,
- relations with critical ICT providers,
- assigned resources, and
- deadlines.
Ensure that plan is available to all members of the compliance team, and you can update it flexibly if something changes.
A dedicated team is just one click away
Let’s map out and execute an efficient and cost-effective implementation path to a resilient software codebase.
Contact Us
Enhance your software system
The next step is focusing on practical activities:
- introducing processes for secure software development,
- enhancing the security of infrastructure and user data,
- amending agreements with critical service providers,
- establishing, presenting, and testing an incident response plan,
- and other critical measures.
Because completing the entire scope in one take is impossible, you should prioritize tasks based on their criticality for meeting compliance.
Focus on continuous monitoring
When the system is up and running, constant monitoring of potential threats and vulnerabilities based on uniform processes and procedures is necessary. The monitoring team should also assess third-party risks and record all ICT incidents.
Conduct testing and audits
Your organization needs to perform comprehensive security testing and audits regularly to ensure your software system remains secure and resilient against known and unknown threats.
Implement training for responsible employees
Enhancing knowledge acquisition and sharing for employees responsible for DORA compliance monitoring is crucial. Provide access to necessary security training and discussions on security challenges to ensure that single team members understand security risks and how to minimize them.
6 How Can IT Craft Help You with DORA Requirements?
IT Craft prioritizes software security on its FinTech projects and is here to help you prepare for the technical side of DORA compliance. We can provide different services to help you identify gaps, map out and implement improvements, or monitor your DORA-compliant software.
Our services aimed at meeting your unique business challenges and project requirements include:
- IT consulting
- MVP development
- DevSecOps and infrastructure monitoring
- app modernization
- digital transformation
- API development
- staff augmentation
- and more
Our company can help you determine a specific combination of the required actions based on the details of your request and deliver any tech help across the entire software development lifecycle.
Limpid Markets
Limpid Markets is a web solution that helps leading banking institutions, such as Morgan Stanley, Deutsche Bank, and BNP Paribas, decrease the communication time needed to exchange pricing information on precious metals.
The client needed
The client had an up-and-running system and required a team capable of its maintenance and expansion while adhering to high coding standards.
How we helped
IT Craft developers took over the client’s software after successfully completing the initial pilot task. They helped the client with seamless 24/7 operations across all time zones and added features that end users required.
! Final Thoughts
Meeting DORA standards will help you enhance software security and resilience, and can be an effective response to growing cyber threats and challenges.
It helps you create a holistic approach to software development, maintenance, and management of third-party service providers/components and lets you minimize security incidents and related penalties.
Ultimately, an increased security level will help you win business partners’ and customers’ trust in your financial services and a better market position.
FAQs
DORA is a new framework that addresses a gap in EU financial regulation and encourages financial institutions to invest in:
- information and communication technology risk management
- reporting major security incidents
- digital operation resilience testing
- managing third-party risks associated with information technology service providers
- sharing information on cyber threats and vulnerabilities
The five pillars of DORA regulation include:
- information and communication technology (ICT) risk management and governance
- incident response and reporting
- digital operational resilience testing
- ICT third-party risk management
- voluntary information sharing
Here are the key steps to meeting DORA compliance:
- Study DORA requirements to identify which apply to your organization.
- Assess your system to determine which requirements to processes, code, and infrastructure management are already in place and which you must implement.
- Prepare a compliance plan while prioritizing single activities based on their severity.
- Enhance your software system by implementing the designed plan.
- Switch to continuous monitoring to ensure the system remains secure and resilient.
- Conduct testing and audits to identify emerging risks and areas for improvement.
- Encourage employee training to increase your employees’ awareness of cyber security.
The key points of DORA regulation include:
- harmonizing security rules and tech standards of the EU financial industry
- improving IT security of financial organizations and their important third-party suppliers
- enhancing operational resilience of systemic financial organizations to help them withstand disruptions




