Constant enhancement of web application security is an essential part of expert-level web app development services, as finding the right security implementation to respond to emerging threats can be challenging.
According to the key findings from the 2024 Crowdstrike’s report on the state of application security, businesses often choose delivery speed to meet time-to-market challenges and drive revenues from cloud solutions.

However, a lack of security focus can create high, long-term risks of data breaches. If you want to rethink your security policy, the best time is now. Check out the required steps and web security best practices below.
1
What Is Web Application Security?
Web application security, or Web AppSec, is a set of practices developers implement to protect websites, web apps, APIs, and infrastructure from malicious activities (data theft, breaches, ransom, and more) and ensure their correct function even under attacks.
As such, web security is highly complex and can vary in strategy and implementation. Web application security measures require a wide range of processes, tools, best practices, and controls needed to:
- design secure web app architecture
- produce and deliver secure source code
- actively discover and eliminate emerging vulnerabilities
- monitor and protect app infrastructure and surface against known threats
- prepare to detect and defend software from previously unknown threats
- design and improve an incident response plan
- provide end users with guidance on keeping their data and accounts secure
- and more
Depending on the project size and severity of security requirements, security checks can be implemented as a separate stage of a software development life cycle or integrated into all development/maintenance activities.
The core web application security tools and measures include:
Web application firewalls
These instruments analyze incoming requests and user traffic to detect suspicious activities, filter malicious traffic, and block common cyberattacks.
Input validation
The web system must check user input against predefined criteria and allow only acceptable inputs, ensuring it is safe for further processing. It enables the system to eliminate direct data manipulation.
Access control
The system must ensure that only authorized users can access certain data or functionality based on their roles and permissions. Multi-factor authentication is also required to decrease the risks of breaches.
Secure architecture and coding
To minimize threats, developers need to use multiple web development security best practices, such as zero-trust architecture, secure data handling, code reviews, comprehensive security testing, timely updates of third-party packages, and more.
Constant monitoring
The development team needs to monitor and log system activities to detect deviating behavior, e.g., unforeseen data exchange with external services. It should also track user sign-ins and activities in the system to encounter compromised accounts.
2
Why Is it Important to Keep Web Applications Secure?
Web security is critical for today’s world economy as users need applications to manage many aspects of their lives, including:
- work,
- shopping,
- entertainment,
- food ordering,
- medical appointments,
- communication,
- banking and personal finances,
- and much more
As a result, web systems store and process vast amounts of valuable user and business data, which makes them priority targets for cybercriminals. Here is concerning statistics on global data breaches in 2024 collected by IT Governance:
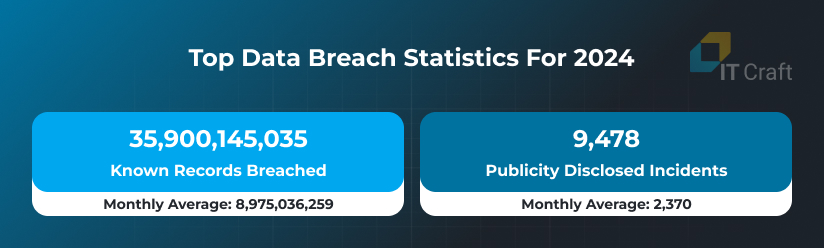
Source: Global Data Breaches and Cyber Attacks in 2024 by IT Governance
Let’s check out the key reasons for maintaining high web application security standards:
User trust
High web app risk protection can motivate users to engage with the app and share personal information. Conversely, successful cyberattacks resulting in stolen user data can severely damage business reputation and cause user churn.
Costs
Eliminating vulnerabilities and blocking cyberattacks costs less than cleaning up the aftermath of an attack from app code and infrastructure.
Uninterrupted operations
Cybercriminals can paralyze a business for many days by causing downtime, hijacking control over infrastructure, encrypting data, and more.
Regulation sanctions
Businesses can face hefty fines for failing to meet web application security standards and allow data theft, especially in regulated industries, such as finance or healthcare.
3
Common Web Application Security Threats
Web applications face many security threats that can lead to data leaks, interception of software control, and other dangerous events. Attackers can exploit weaknesses in:
- app source code,
- architecture,
- infrastructure,
- APIs,
- third-party packages, and
- user experiences.

Brute force
A brute force attack means trying all possible combinations until the attacker finds the correct one. It is usually automated through scripts or bots and targets user passwords, API keys, and SSH logins.
SQL injection
Attackers type malicious SQL queries into user input fields, which let them gain unauthorized access to the database, receive permissions, or manipulate/destroy important data.
Zero-day vulnerability
Zero-day exploits present unknown or unaddressed flaws in operational systems, firmware, or hardware, which cybercriminals use to plant malware or access user data. They try to use zero-day vulnerabilities quickly before security vendors publish patches.
Cross-site request forgery (CSRF)
Cross-site request forgery involves injecting malicious code into a logged-in user’s browser. This allows the attacker to take actions on a website or app without the user’s knowledge.
Cross-site scripting (XSS)
An attacker injects a malicious script into a legitimate app or page and executes it in the client’s browsers to gain access to the user account, extract valuable data, or impersonate the user.
Distributed denial of service (DDoS) attack
Attackers try to overload app infrastructure with too many requests or traffic to cause service downtime and its unavailability to real users or potential exposure of sensitive data.
Credential stuffing
Attackers try to quickly use large lists of login/password combinations obtained through a data breach or purchased in the dark market to find a valid one and access a user profile.
Memory corruption
App developers can unintentionally insert memory corruption bugs, which attackers try to sniff out and exploit by injecting malicious code or initiating buffer overflow/modification attacks.
Weak passwords
An old but common problem is that users create too-simple passwords. Or they can use personal information as a password that can be easily reconstructed, or one password for many services.
Third-party code abuse
Cybercriminals can compromise widely used open-source to target multiple businesses or look specifically for businesses using obsolete and, thus, vulnerable libraries to get easy access to software code.
Service misconfiguration
Attackers can study a business’s infrastructure to find servers with improper security configurations to break into the perimeter and gain access to a part of or the entire infrastructure.
Insecure data storage
Developers may store sensitive user data without strong enough encryption to meet business needs or precipitate feature shipment, leading to exposure and theft of sensitive data.
Need help with improving your web application security features?
Let’s discuss your concerns and find a cost-effective way to make long-term improvements to your software.
Contact Us
4
Web Application Security Tools
Because threats are numerous and versatile, 90% of security professionals use 3+ tools to manage their responsibilities, and some teams rely on 25+ tools to detect threats. Here are some of the instruments that can help enhance web application security:
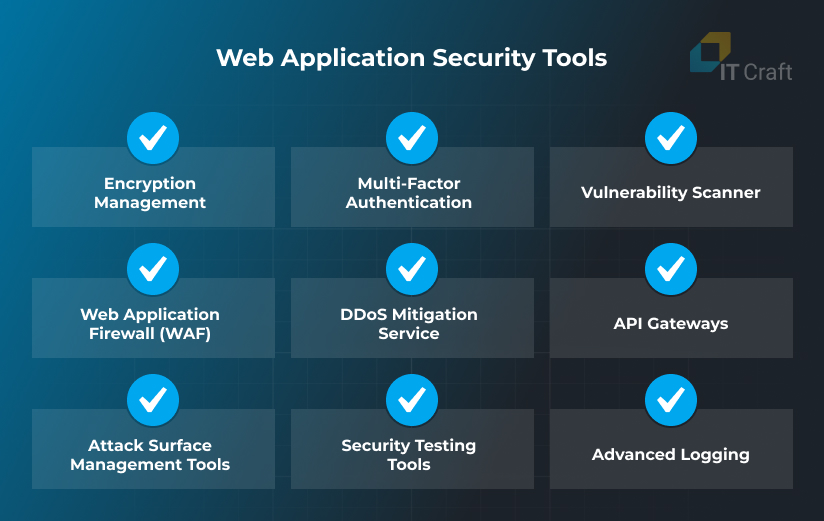
Encryption management
Encryption management tools allow the project team to handle generation, distribution, and storage of encryption keys, ensuring access to sensitive data only to authorized users.
Multi-factor authentication
An extra verification step, using a different method, allows businesses to decrease the chances of a breach even if credentials are compromised.
Vulnerability scanner
Developers can scan website or app source code for common vulnerabilities automatically. Advanced vulnerability scanners can also help with checking third-party dependencies.
Web Application Firewall (WAF)
WAFs stand between users and web applications, blocking and filtering malicious traffic before it reaches the applications. As a result, cyber thefts cannot exploit many vulnerabilities.
DDoS mitigation service
DDoS mitigation services focus specifically on filtering high volumes of malicious traffic, for which they have extremely high broadband capacity and flexibly adapt to attack patterns.
API gateways
API gateways gather requested data from one or more back-end services and send it to the client app. As a single entry point, they provide an additional web app risk protection layer.
Attack surface management tools
Attack surface management tools help engineers control the entire app infrastructure and remediate vulnerabilities.
Security testing tools
Testing tools help automate and execute different security testing activities to identify flaws and vulnerabilities early.
Advanced logging
Logs are essential for identifying attacks. Engineers use logging solutions to collect diverse data on system state, search and filter entries, receive immediate alerts on unusual behavior, and more.
5
Key Web Application Security Requirements
Web application security requirements are crucial for both establishing development processes and building high-quality source code. They serve as a web application security guide to the entire team on what single members should complete to protect the software against cyber threats.
Here are key points on basic security requirements from the SANS’s checklist on building secure web applications that you can use for formulating and expanding requirements to your web solution:
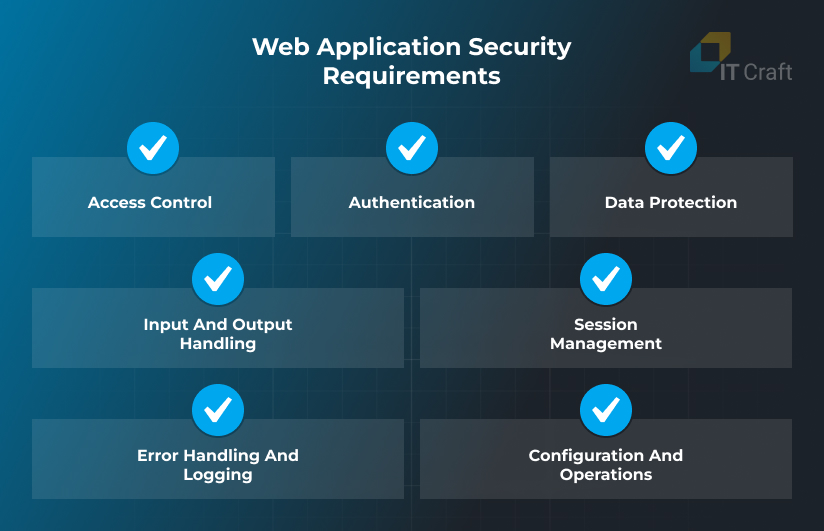
Access control
The system should consistently check access through a centralized service, ensuring only authorized users can reach sensitive data. It should use the principle of least privilege and deny access to unauthorized data/functionality depending on user roles.
Also, developers should not use mechanisms attackers could use to increase their access rights, or place redirects leading users to malicious websites.
Authentication
The team should implement a strong user authentication policy and password reset system to prevent identity theft. They should store credentials securely with minimum access and never hardcode them in the app code.
The web app must be prepared against brute force attacks by activating account lockout after several unsuccessful attempts.
Data protection
Software engineers need to encrypt data at rest and in transit, use secure connections where possible, and configure servers with strong TLS. They also need to establish a secure channel for key exchange and store user passwords by adapting hashing techniques combined with salt.
Also, it is wise to process and store only necessary user data.
Input and output handling
The system should validate user input and uploaded files to prevent SQL injection and XSS attacks. Tokens can help against CSRF attacks, providing random and unique identifiers that criminals cannot analyze and forge. Also, the team should promote allowlists over blocklists to improve the blocking of malicious inputs.
Session management
Software developers should generate random identifiers to eliminate prediction. They also need to implement automated logout for inactive users after a certain period. They need to put logout options in a visible place and destroy associated session data to evade accidental revival.
Error Handling and Logging
The team should provide only general information in error messages to hide clues from attackers about how the system works. Developers should also customize default error messages from frameworks for the same reason.
The system needs to log all authentication activities, attempts, and changes of user privileges as well as reaches of sensitive data.
Configuration and operations
The development team should establish rigorous processes and improve them regularly. It should conduct code reviews, execute security testing, and properly configure all software infrastructure. Also, developers should prepare and test an incident response plan, which they should update based on emerging web application security issues and solutions.
6
Web Application Security Best Practices to Follow in 2025

Organizations can face multiple obstacles when responding to threats due to the high complexity of web technologies and constantly emerging security challenges to which they must adapt.
Let’s discuss web application security tips that can help the development team build and maintain a sustainable approach to managing security threats:

Visibility
Your organization requires full visibility of your web system, infrastructure, environments, and data you process and store to understand risks and challenges. This holistic view of the system and the connections between its single components will help you identify security gaps, improve vulnerability management, and streamline security monitoring.
Security Tools
According to The State of Security Remediation report, 61% of organizations use 3 – 6 detection tools, but only 24% feel prepared for cybersecurity threats. Too many security tools can overwhelm the team, creating unnecessary complexity and alert fatigue. It is wise to decide on minimum basic tools for identified gaps and add new tools only if they provide more benefits.
Reviews and audits
A lack of code reviews fueled by the need to ship features as fast as possible can result in vulnerabilities going overlooked and slipping into production code, which is why code reviews should not be skipped.
As part of web development security, the development team should also complete regular audits of source code, infrastructure, and third-party packages.
Documenting
The development team needs to describe thoroughly in project documentation:
- system architecture,
- development and QA processes,
- security guidelines, and
- results of audits
It also must regularly update project documentation to maintain system visibility in the long term.
Prioritization
The dedicated development team needs a unified approach to vulnerability triaging and threat prioritization to respond to critical threats quickly. This is why security experts should design and implement a prioritization strategy to ensure timely remediation and minimal risks of too-long threat exposure.
Process reconsideration
Cyber threats evolve and require constant rethinking of the implemented security approach and techniques to meet them. But there is also another point. Incremental process improvements enable a team with limited resources to move gradually from a quick-fix approach to long-term sustainable solutions for managing threats and boosting productivity without sacrificing security.
Automation
Automation is critical for managing growing complexity under limited time and resources while reducing pressure on the project team. Automation can be applied to:
- code reviews
- security testing
- secure deployments
- threat detection
- decreasing alerts and false positives
As a result, automation can help reduce the number of code/infrastructure issues and improve remediation time.
Training
Even if the project has a dedicated security team, security training and knowledge sharing between all team members are important. Training can help the team build secure code in less time, respond to discovered threats quicker, and prevent vulnerabilities from recurring after remediation.
Data handling
The team should implement data encryption where possible and use secure connections. Moreover, the development team should collect only necessary user data and never store redundant sensitive information. The team must also depersonalize any data that will be used for software testing.
Compliance
The project team must prioritize regulatory compliance on data collection, processing, storage, and transmission throughout the entire software development lifecycle. It also needs to check changes in regulations regularly and adapt the system to them on time.
Are you looking to launch a secure web service?
Let’s estimate the required implementation path and budget.
Contact Us
7
Enhancing Web Application Security with IT Craft
IT Craft engineers focus on security threats and risks while working on client projects, as we know that implementing robust web application security features is key to earning end users’ trust.
Our teams complete a wide range of activities needed to maintain high-security standards at any stage of software development life cycle:
- code review and app security audit
- IT consulting
- regulation-compliant web development
- web project rescue and improvement
- app modernization and rearchitecting
- DevSecOps
- AI development
We are here to help you solve your security challenges, such as meeting regulatory compliance, enhancing software infrastructure, organizing secure data storage, closing vulnerabilities in source code, and beyond.
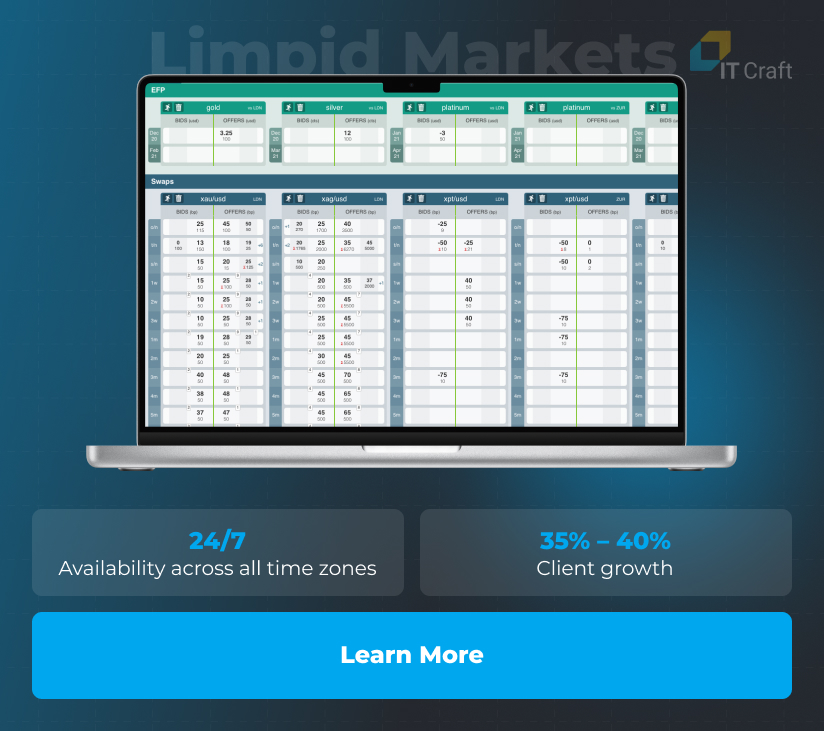
Limpid Markets
This web-based marketplace enables major participants of London and Zurich over-the-counter interbank markets to quickly exchange pricing information and decrease costs of single deals.
The client needed
The client was looking for a team that was capable of taking over their up-and-running web system and ensuring its high security as well as seamless operations 24/7.
How we helped
The IT Craft team completed both a system analysis and a pilot task, demonstrating adherence to high-security standards. It continues working on project expansion and maintenance, emphasizing source code security.
!
Conclusion
Your organization should constantly work on identifying web application security issues and solutions, including:
- monitoring risks and threats
- creating and updating project documentation
- auditing code, tools, and processes
- listing and prioritizing vulnerabilities, inefficiencies, and areas for improvements
- using encryption and role-based restrictions where possible
- automating testing, checking, and monitoring tasks
- providing the project team with training and web application security guides
These steps will help your organization focus on a long-term response to security challenges and minimize risks of severe breaches.














