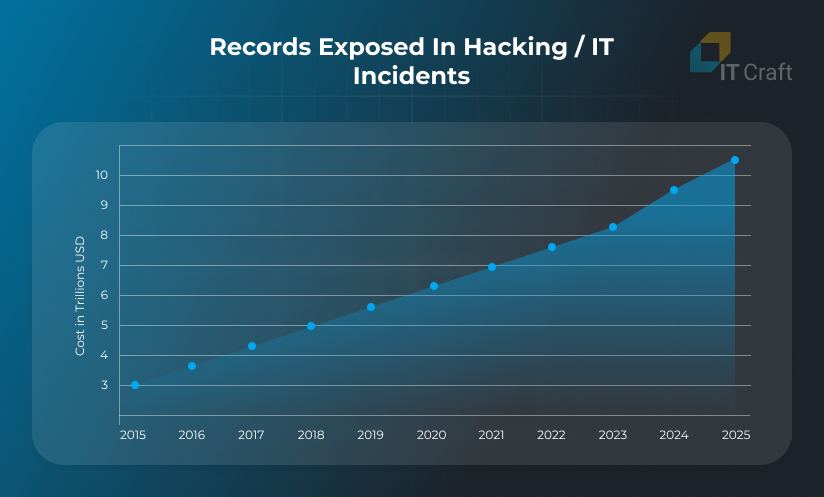
As cybercrime costs are projected to reach a staggering $10.5 trillion annually by 2025, mastering security in software development has never been more urgent. This article will explore essential best practices for securing your development process in 2025.
From vulnerability management to security testing, discover the latest tools and approaches that empower your team to build applications that meet and exceed today’s security standards, ensuring robust data protection and user trust.
1 What Is Secure Software Development?
Secure software development integrates security throughout the software development lifecycle. Each phase needs to consider possible threats and vulnerabilities—from concept to deployment—to reduce risks to users and the business. The main goal is to make the software fully functional yet secure from malicious attacks.
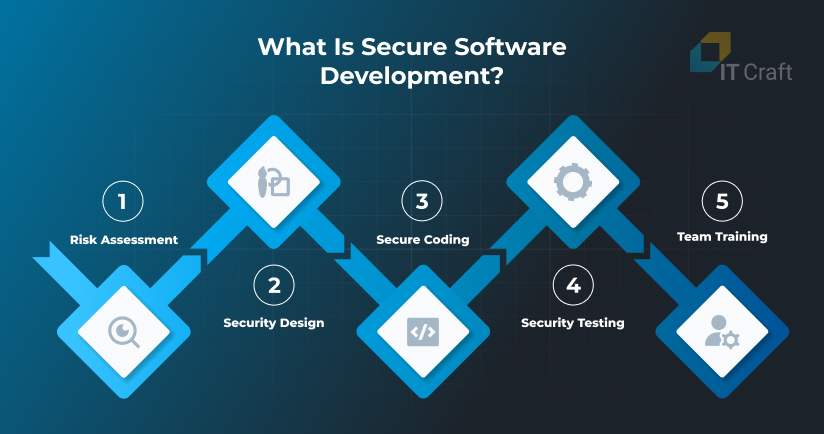
This process includes several key steps:
- Risk Assessment: Identifying potential threats to the application and analyzing the possible impact on data security.
- Security Design: Implementing secure practices during the application's architectural design to avoid vulnerabilities.
- Secure Coding: Adhering to security standards during code writing, including data validation and prevention of SQL injections.
- Security Testing: Regularly conducting vulnerability tests to detect and address issues before product launches.
- Team Training: Continuously educating the development team about new threats and security assurance methods.
Secure software development is an ongoing secure software development process that requires attention at all stages of development. It protects data and enhances user trust, which is very important in today’s digital environment.
2 Importance of Security in Software Development
Security must come first in software development to protect sensitive data and build customer trust.
According to the 2023 Allianz Risk Barometer, which analyzed input from over 2,700 risk management experts across 94 countries and territories, 45% of professionals identify cyber incidents as the top threat to business continuity, surpassing concerns over natural disasters and energy issues.
By implementing robust software development security measures, organizations can safeguard their applications against cyber threats and ensure a secure user experience.
Protecting Sensitive Data
Securing software is crucial as cyber threats grow more sophisticated. With businesses relying heavily on applications, a security breach can lead to severe financial, reputational, and legal consequences.
Protecting sensitive data is essential, especially with privacy laws like GDPR and CCPA requiring strong safeguards. A single breach can result in heavy fines and loss of invaluable customer trust.
Maintaining Software Integrity
Another reason security becomes important in software development is the integrity of the software itself. Software vulnerabilities can result in unauthorized data access, manipulation, or even complete system compromises.
A secure development lifecycle thus helps organizations prevent such vulnerabilities and ensures that applications are resilient against attacks.
Cost-Effective Security Measures
Also, security measures during the development phase can save costs in the long run. It is much more cost-effective to catch and address vulnerabilities early in the development cycle than to deal with the aftermath of a security incident.
Proactive vulnerability reduction improves security posture and contributes to operational efficiency.
Integrating Security into Development Frameworks
Furthermore, integrating security into these frameworks becomes essential as more organizations adopt agile and DevOps methodologies. Continuous security assessments and automated testing can help identify real-time vulnerabilities, allowing developers to address issues quickly and efficiently.
This shift towards a security-first mindset fosters a culture of security awareness among security software development teams, leading to more secure coding practices.
Secure Your Software Today
Implement top security practices to safeguard your applications. Let our experts help you build a secure software development process.
Get Started with Security Experts
3 Secure Software Development: Best Practices
Discover the essential security in software engineering practices that safeguard your software applications. These best practices, from secure coding standards to regular security testing, help mitigate vulnerabilities and protect sensitive data.

Zero-Trust Architecture
2024 is the year to turn zero-trust architecture (ZTA) into action. Based on “never trust, always verify,” ZTA requires every access request to be authenticated, authorized, and encrypted. By 2026, Gartner predicts that 10% of large enterprises will have mature zero-trust programs, up from under 1% in 2023.
- Micro-Segmentation: Divide your cloud into isolated segments to limit attack spread, containing breaches within single areas.
- Continuous Monitoring: Use AI-driven monitoring to detect suspicious activities and respond quickly. IBM reports that AI-powered security can cut breach costs by up to $2.22 million.
Input Validation
One of the most critical security practices is input validation. This involves ensuring that all user inputs are properly validated before processing. By filtering and sanitizing inputs, developers can prevent malicious data from being executed in the application, significantly reducing the risk of attacks.
Authentication and Authorization
The data can, therefore, be protected with strong authentication and authorization mechanisms. The practice of multi-factor authentication can further facilitate this; it may make your authentication systems more secure.
Also, role-based access control (RBAC) can allow users to have only the resources based on their role and, as a result, reduce unauthorized access.
Encryption
Data encryption is a vital security practice that protects sensitive information in transit and at rest. Utilizing strong encryption algorithms helps safeguard data from interception and unauthorized access, ensuring that even if data is compromised, it remains unreadable without the appropriate decryption keys.
Quantum-Safe Cryptography
Quantum computing threatens traditional encryption, with potential security breaches expected by 2030. Forward-thinking companies should start exploring quantum-safe encryption now.
- Post-Quantum Cryptography: Invest in quantum-resistant algorithms to secure data against future threats.
- Hybrid Encryption: Combine classical and quantum-safe encryption for added security during the transition.
Security Monitoring and Incident Response
Continuous security monitoring allows organizations to detect suspicious activities and respond swiftly to security incidents. Establishing an incident response plan ensures teams are prepared to handle breaches effectively, minimizing damage and recovery time.
DevSecOps
DevSecOps means weaving security into every development step—not just shifting left.
- Automated Security Testing: Deploy automated tools for ongoing security checks, catching vulnerabilities early to reduce later costs.
- Security-As-Code: Write security policies as code for consistent, scalable security across environments, enabling quick deployment while upholding standards.
Enhance Your Software Security
Protect your business and users with industry-leading security practices. Learn how we can help secure every stage of development.
Talk to a Security Expert
4 Most Common Security Risks in Software Development
Software application security is more critical than ever. As organizations increasingly rely on digital solutions, understanding the most common security risks becomes essential to protecting sensitive data and maintaining user trust.

Injection Attacks
One of the most pressing threats in security software development is injection attacks. These occur when an attacker inserts malicious code into an application, which the system can execute. The most notorious forms of injection attacks include:
- SQL Injection: Attackers manipulate SQL queries to access or alter database content, potentially exposing unauthorized data.
- Command Injection: This allows attackers to execute arbitrary commands on the server, leading to potentially devastating consequences.
Cross-Site Scripting (XSS)
Another significant threat is cross-site scripting (XSS), which involves injecting malicious scripts into web pages viewed by users. Key points include:
- Attackers can steal cookies, session tokens, or other sensitive information.
- This allows them to impersonate users and compromise accounts, severely undermining the trustworthiness of a web application.
Broken Authentication and Session Management
Broken authentication and session management are critical risks that can lead to unauthorized access. Important considerations are:
- Weaknesses in authentication processes, such as poor password policies or lack of multi-factor authentication, can enable attackers to hijack user accounts.
- Issues with session management, such as insecure cookie handling or session fixation, can allow malicious actors to take over active user sessions.
Sensitive Data Exposure
The exposure of sensitive data is another pervasive risk. Key aspects include:
- Inadequate encryption practices can leave sensitive information vulnerable during transmission or while stored.
- Organizations must prioritize protecting personal data to comply with regulations like GDPR and avoid severe penalties.
Security Misconfiguration
Security misconfiguration is a common oversight that can occur at various levels of the application stack. Key points include:
- Default configurations are often not secure.
- If systems are not properly hardened or patched, they can become easy targets for attackers.
- Regular audits and secure configuration guidelines are essential to mitigate this risk.
Insufficient Logging and Monitoring
Another critical aspect is insufficient logging and monitoring. Without comprehensive logging:
- Organizations may fail to detect unauthorized access or anomalies in system behavior.
- This can result in delayed responses to security incidents, allowing breaches to escalate before they are addressed.
- Implementing robust monitoring tools and establishing clear incident response protocols can significantly enhance an organization’s ability to detect and respond to threats.
Cross-Site Request Forgery (CSRF)
Cross-site request Forgery (CSRF) is a risk where an attacker tricks a user into executing unwanted actions on a different website where the user is authenticated. Key measures include:
- Implementing anti-CSRF tokens to prevent such attacks.
- Educating users about the risks of CSRF and how to recognize potential threats.
Insecure Deserialization
Insecure deserialization is another vulnerability that allows attackers to manipulate or inject malicious data into applications. Important strategies include:
- Ensuring robust data validation during deserialization to prevent remote code execution or other severe exploits.
- Implementing safe serialization practices to mitigate this risk.
Using Components with Known Vulnerabilities
Moreover, reliance on third-party libraries and components can introduce known vulnerabilities into an application. Key actions include:
- Regularly updating these components to protect against known exploits.
- Monitoring for security advisories related to third-party libraries to maintain a secure application environment.
! Conclusion
Robust security in software development is crucial in today’s digital landscape. Organizations can effectively mitigate risks and protect sensitive data from cyber threats by adopting key security best practices.
This proactive approach enhances application security and builds user trust, ensuring long-term success in an increasingly security-conscious environment.
FAQs
This points to the role of security in software development: securing applications from vulnerabilities and threats across the development life cycle. Security ensures data confidentiality, integrity, and availability; hence, it is critical in software development.
SSDLC stands for Security Software Development Lifecycle. It’s a platform for infusing security practices into software development’s planning and design, implementation, testing, and deployment phases. This is crucial as it will help the organization mitigate security risks in software development.
These would be the most important principles: least privilege, secure coding practices, vulnerability testing, and updating to address security issues in software development—all good practices for maintaining a strong security posture in software development.
To secure software development, organizations should adopt secure software development best practices, conduct regular security testing, implement strong authentication mechanisms, and maintain up-to-date libraries and frameworks. Integrating security into the software development and security process is essential for effective risk management.
The three types of software security include application security, which focuses on securing applications from threats; network security, which protects the underlying network infrastructure; and data security, which ensures the protection of sensitive information at rest and in transit. Together, these types form a comprehensive approach to security in software development.


