Integrating the highest cybersecurity standards into healthcare software development, maintenance, and operational processes is crucial for every healthcare organization and the industry, although standards are already high.
In a survey completed by SecurityScorecard among the top 500 publicly traded US healthcare companies, 48% of organizations received an A rating (90-100 scores), and only 1% of organizations received an unsatisfactory F rating (<60 scores).
The industry itself was estimated to have an overall B+ security rating.
However, being less than perfect may be insufficient. Organizations with a B (80-89) rating are 2.9 times more likely to face a data breach than A-rated organizations.
Let’s discuss the challenges, specifics of cybersecurity in healthcare, strategies, and regulations below to help you take your next step toward a protected software and infrastructure environment.
1
Why Is Cybersecurity Important in Healthcare?
Cybersecurity is critical for uninterrupted operations. Organizations must protect sensitive electronic information, digital infrastructure, and software from malicious activities aimed at unauthorized access.
The key factors determining high requirements for cybersecurity in healthcare include:
High Costs of Successful Cyberattacks
Healthcare organizations are valuable targets, and healthcare is the top industry for many of them. The Privacy Rights database recorded that 32% of all breaches happened in healthcare.
The average cost of a single breach also breaks the record. It has increased by 8.2% in 2023 compared to 2022, reaching $10.03M in financial losses.
Far-Reaching Consequences of an Attack
Data security is not just an issue faced by IT departments but an enterprise risk that demands appropriate attention.
The magnitude of an attack can be high if cybercriminals access essential software, e.g., an EHR system or an interoperability platform, causing disruptions in an organization’s performance, interconnected companies, and, ultimately, affecting the entire industry.
Eroded Trust and Sanctions from Regulators
Large data breaches and leaks can severely damage an organization’s reputation, leading to customers’ and partners’ mistrust.
Also, legal actions are another aftereffect. Healthcare organizations can face fines and penalties from regulators for failing to meet compliance requirements.
Increased Value Generated through Cybersecurity Improvement
The positive point is that organizations can generate four times more shareholder value by reaching advanced cybersecurity performance levels when compared to basic and intermediate levels, according to a Diligent Institute and BitSight study.
2
Why Is the Healthcare Industry under Constant Cyberattacks?
Sadly, healthcare outperforms other industries in the number of attacks, which has doubled within the last five years:
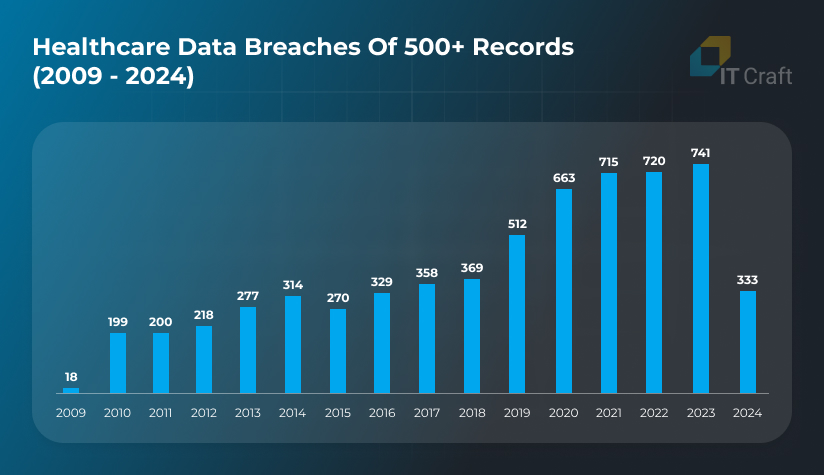
Source: HIPAA Journal
Also, 2023 was the worst year in the number of exposed healthcare records, affecting many patients:
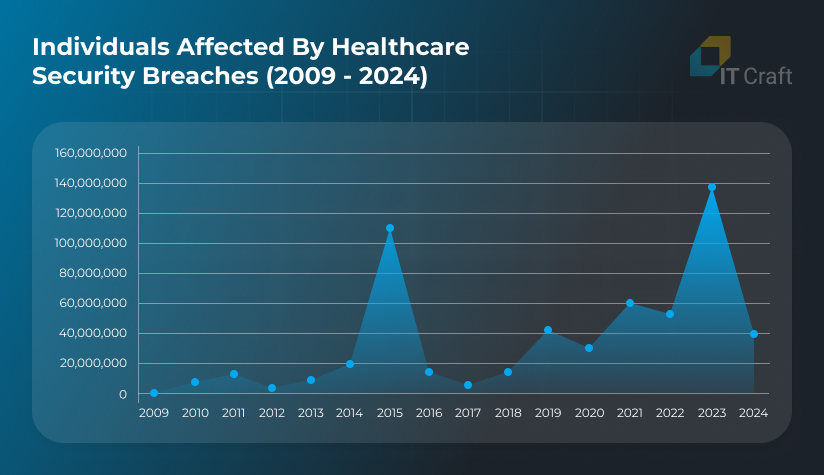
Source: HIPAA Journal
Let’s analyze what makes healthcare organizations one of the most valuable targets:
High Value of Patient Data
The dark market values medical records highly. Cybercriminals can sell stolen medical records for $400-$500 or even $1,00 each, while a credit card is worth only $1–$5.
Patient records contain sensitive patient and payment data, which can be used for identity theft, fake prescriptions, and financial and insurance fraud. Unlike credit cards, medical records cannot be blocked immediately. Hence, the lifespan is longer and can bring cybercriminals high returns.
High Costs of Disruptions
A successful cyberattack can easily affect several interrelated healthcare organizations, including clinics, practices, pharmacies, senior living facilities, suppliers, and more, potentially leading to devastating results and increasing cybercriminals’ chances of ransom payment.
A notorious example is Change Healthcare, an organization that paid $22M to a ransomware gang in March 2024. While many refuse to pay, such cases incentivize criminals to continue their attacks.
Wide Attack Surface
Cybercriminals have a wide choice of entry points at their disposal, which include:
- web and mobile medical apps and their cloud infrastructure
- connected IoT and medical devices
- internal networks
- interoperability platforms
- employee devices
- Wi-Fi hotspots inside clinics
and more.
Each of the above points requires different security measures and can become vulnerable easily if an organization does not have enough resources to track threats and update points quickly.
Non-Optimized Processes
Unoptimized workflow can be a source of weakness. Employees can be overworked and lose their focus, not recognize suspicious emails, or give cybersecurity a low priority.
Clinics staff can use shortcuts by sharing credentials with their colleagues, keeping passwords on their desktops or in messengers, or they can leave corporate devices unattended.
Medical staff may require training, which could raise their awareness of detecting threats and elaborate protocols for what to do if they make a mistake.
Healthcare Digital Transformation
Last but not least, timely digital transformation is crucial for security. Health organizations using legacy software are prone to cyberattacks, so using the latest technologies is necessary.
Also, access management can be slow or inefficient, and single team members receive access rights to the information they do not require to perform their duties, thus creating an additional entry point for cybercriminals.
3
How Do Organizations Implement a Cybersecurity Strategy?
Healthcare organizations need to design, implement, and regularly update a multifaceted cybersecurity strategy to protect themselves from emerging threats and accidental leaks.
As an organization, you should include the following steps in your cybersecurity strategy:
Understand Threat Landscape
You need to check current threat trends and their possible consequences for your system.
To do this, you need to identify and prioritize the types of cyberattacks your organization is likely to experience (ransomware, phishing, stealing physical devices) and their severity.
Assess Your Cybersecurity
As the next step, evaluate your current level of readiness for cyberattacks and compliance with regulations. Identify gaps, improvement areas, and set measurable KPIs. Also, examine employee’s awareness of existing threats and their responses to them.
Assess Ways of Enhancing Cybersecurity
Check which tools and expertise you have and which you lack to close gaps and improve areas, increasing your cybersecurity level. Consider hiring outsourcing experts if the required skills are unavailable in-house.
Design a Plan
Prepare a detailed cybersecurity plan that contains identified threats, risks, improvement areas, security procedures, and practical steps to threat prevention in healthcare. Discuss the plan with stakeholders and get their approval to eliminate the possibility of internal resistance to changes.
Implement the Plan
Work on gradual enhancements while moving from the most to least prioritized tasks to decrease the level of threat exposure. To increase security, integrate required security policies and solutions and provide relevant employee training. Use zero-trust architecture and defense in depth to minimize the consequences of a potential data breach.
Evaluate Results
When the security measures are in place, you need to reassess the security implementation against the initial plan to ensure you have reached the envisaged KPIs and the security level has increased.
Monitor and Update
Continuously monitor your software and infrastructure to identify concerns, vulnerabilities, and weak spots, and work on quick updates to be faster than cyber criminals.
Audit Your System
Ensure regular system audits every 3–6 months, using penetration testing to examine the system against old and emerging threats and identify new improvement areas. Engaging internal and external teams to exclude a biased outlook is wise.
Do you need help with determining cybersecurity measures?
Let’s assess your system and decide on practical steps that improve your system’s cybersecurity.
Contact Us
4
Who Are Main Healthcare Stakeholders?
A big challenge of cybersecurity in healthcare is that there are many potential targets. As a highly integrated industry, healthcare has a wide range of valuable stakeholders, including:
- Patients – cybercriminals seek access to patients' medical accounts for identity theft and financial fraud.
- Doctors and clinic staff – are direct targets whose credentials let criminals sneak into internal systems.
- Administrators – reach comprehensive information about processes, costs, taxes, and benefits, patient history, staff workload, and more. Also, it becomes easy to halt all operations.
- C-level executives – a successful attack can unveil invaluable insider information.
- Vendors and suppliers – they may use inferior security standards, and while connecting to the clinic's system, their software may become an entry point.
- Pharmacies and pharmaceutical enterprises – they are also the main targets, as they open access to prescription information, controlled substances, and more.
- Equipment manufacturers – access to connected equipment can be used to disrupt operations and force healthcare organizations to pay ransom.
- Insurance companies – they can suffer from financial fraud through false claims.
- Technology developers – cybercriminals can paralyze the entire industry by breaching a major software vendor. A little vendor can be used to break into a clinic's internal network.
- Regulators and policy makers – an unlikely target for individual criminals but a priority for international crime and state-backed hacking groups.
Therefore, cybercriminals have a wide selection of targets, besides a wide surface for possible attacks, which makes reaching high standards of cybersecurity in healthcare even a higher priority.
5
Understanding Types of Threats
Cybercriminals can use the following tools and methods to cyberattack a healthcare organization’s software system, which they can combine within one attack:
Phishing
Phishing is one of the widest-used attack types. It occurs when a criminal uses social engineering to send a legitimately looking email and make the victim click on a malicious link or an infected attachment.
Exploitation of vulnerabilities
Criminals can access internal networks by identifying and exploiting human errors and inefficiencies, such as exposed misconfigured servers, lack of latest updates, OS zero-day exploits, brute force attacks on weak passwords, etc.
Credentials theft
Credential theft means stealing login and password details from a system user. These details can be stored in a password manager, an exposed document file, or a paper stuck to a desktop monitor.
Identity theft
Identity theft refers to stealing personal patient or employee information, which is used to impersonate them while making fraudulent financial claims.
Theft of a physical device
A less common but still possible scenario is when a person leaves a device unattended that contains important credentials and is used to access healthcare software.
Ransomware
Criminals infect an organization’s internal system with a virus that encrypts data and disrupts all operations. After taking the system hostage, they demand a ransom for restored access.
Insider-driven attacks
A malicious actor can be an employee who helps gain access to the system or accidentally exposes sensitive data while lacking awareness of best practices for maintaining cybersecurity in healthcare.
6
Key Elements of Cybersecurity in Healthcare
A healthcare organization should establish and manage control and visibility across all key elements of its cybersecurity strategy to protect its infrastructure, identities, and endpoints:
Access Management
- Implement multi-factor authentication
- Reduce the number of accounts with privileged roles to only necessary
- Regularly rotate credentials for authorized accounts
- Timely update or revoke access rights/credentials for employees who change their roles or resign
- Restrict self-registration and enhance the verification process, e.g., through video calls
- Restrict user account from escalating rights and privileges
Software Code
- Introduce a vulnerability management program
- Provide regular code checks against emerging threats
- Emphasize QA and testing for new functionality
Network Security
- Deploy firewalls to block brute force activities
- Set up monitoring software to scan all system activities
- Allow remote access via VPN connection only to authorized human users
- Regularly perform external vulnerability scans to detect exposed system resources
- Improve network segmentation and isolation to prevent the network from further infection in case a breach happens
- Block remote access tools
Enhance your network security with IT Craft
Our experts can help you reconfigure your network and implement best DevSecOps practices to improve your security level.
Contact Us
Data Protection
- Provide enhanced encryption for all data at rest and in transit
- Deploy a data loss prevention system to block unauthorized data transfer
- Use advanced email gateways to filter spam and phishing
- Ensure there is no direct access to backup data, possibly by using both online and offline backups
Medical Devices Management
- Make a list of all connected medical devices and monitor their network activities
- Restrict automatic updates and changes from unknown sources
- Install updates and patches only provided by device manufacturers
Incident Management
- Create and test a response and recovery plan
- Perform system audits and penetration testing to assess the state of security
- Deploy event management tools to detect and alert threats
- Use advanced logging to detect and analyze suspicious activities
- Temporarily deactivate compromised accounts or limit access if deactivation is impossible
Employee Training
- Create a working environment that promotes using best practices on cybersecurity in the healthcare industry
- Provide staff training on implemented policies
- Conduct checks and examinations, ensuring employees understand the workflow
- Create guides and documentation for references
Compliance Management
- Align implemented measures with regulations
- Appoint and empower a person responsible for the organization's cybersecurity
- Review changes in regulations and update your system
7
Healthcare Cybersecurity Challenges
Here are the main concerns you need to keep in mind when improving cybersecurity state within your organization:
Costs
Implementing cybersecurity best practices can be complex and expensive, requiring investment in software development and compliance with regulations, which can be challenging for small and mid-sized organizations.
It makes sense to start with IT consultation and consider outsourcing software development/DevOps maintenance under a limited budget.
Legacy Software
One of the most striking problems in healthcare is the use of outdated systems and technologies. These often contain multiple vulnerabilities and lack comprehensive vendor support.
It is wise to isolate legacy solutions and gradually replace them with up-to-date software.
Cyber Literacy
Another huge concern is the lack of knowledge about cybersecurity in healthcare, especially among low-educated employees, which can prevent them from identifying and defending against a cyberattack.
It is crucial that employees understand the basics of digital operations and workflows, as well as how criminals can exploit specific vulnerabilities to gain access to the system.
UX
Implemented workflows should encourage users to apply best security practices. No matter how important implemented protection measures are, when they frustrate users and take the time users require to complete their work tasks, shortcuts will emerge that could eventually lead to a breach.
When working on security improvements, the project team must always keep usability and convenience in mind, ensuring improvements require minimum user effort.
Cyber Talent Shortage
An indirect but serious challenge, cyber talent shortages press all stakeholders in the healthcare ecosystem and can potentially slow down the pace of cybersecurity improvement.
Outsourcing healthcare cybersecurity to a reliable vendor could help close the gap and reach goals within the envisaged timeline.
8
Cybersecurity Healthcare Regulations Worldwide
Authorities worldwide require health organizations to follow particular standards when collecting, storing, and disclosing sensitive patient information. Major healthcare cybersecurity regulations include:
- HIPAA (Health Insurance Portability and Accountability Act) regulates the handling of patient information in the USA.
- GDPR (General Data Protection Regulation) applies to processing and storing personal information of EU citizens.
- Data Protection Act is mandatory in Great Britain.
- PIPEDA (Personal Information Protection and Electronic Documents Act) protects the rights of Canadian citizens.
- FISMA (Federal Information Security Management Act) is required from the US state agencies administering healthcare programs.
- HITECH (Health Information Technology for Economic and Clinical Health Act) is part of HIPAA policies, which strengthens the use of Electronic Health Records.
Local general and healthcare-specific regulations may apply in other countries, which service providers must integrate when expanding their services.
Also, new regulations emerge to that healthcare organizations must adapt, such as the EU Cyber Resilience Act and DORA (Digital Operational Resilience Act).
9
IT Craft’s Expertise
IT Craft engineers can help healthcare organizations establish and maintain high security standards while protecting software source code, network infrastructure, and user data.
Our company helps service providers with:
- system audit
- IT consulting
- digital transformation services
- system reengineering
- HIPAA-compliant custom software development
- security testing
- DevOps and system maintenance
As a long-term tech partner, we emphasize an Agile, flexible approach to each client’s unique needs for healthcare cybersecurity, helping introduce required improvements quickly and cost-efficiently.
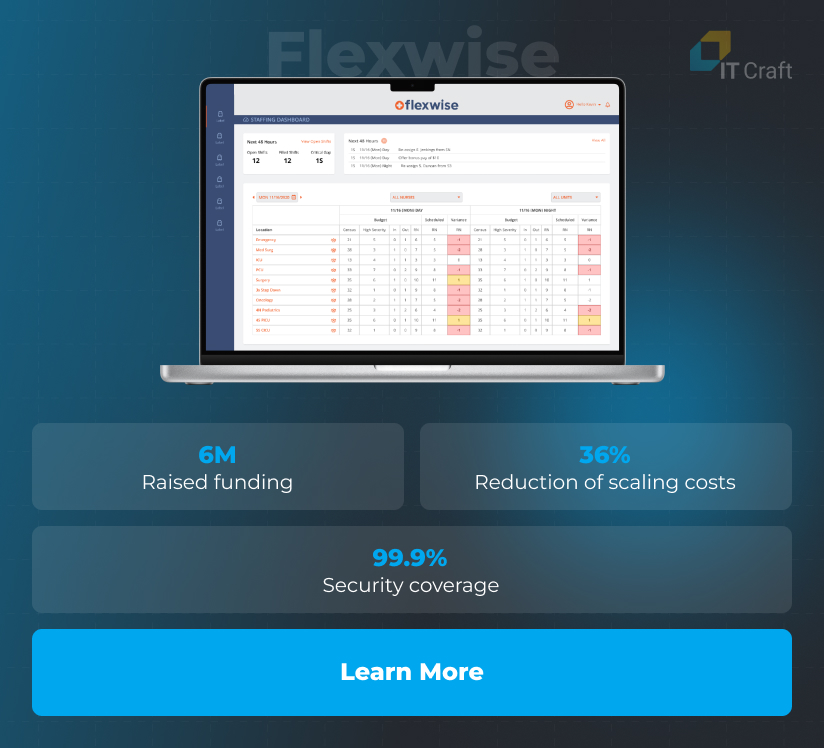
Flexwise
Flexwise optimizes clinics staff management platform, preventing staff under- and overload, and ensuring a transparent administration.
The client needed
The client approached IT Craft with a request for system enhancement and finalization, which IT engineers completed within the estimated timeline.
How we helped
The IT Craft team launched a scalable and flexible HIPAA-compliant system. After the system launch, they focused on expansion, improvement, and maintenance activities to ensure secure system operations.
!
Summary
The importance of cybersecurity for healthcare cannot be overestimated. Healthcare organizations must maintain the highest possible security level and work proactively on security enhancements to avoid the devastating consequences of cyberattacks.
Cybersecurity in healthcare requires relevant expertise in a wide range of interrelated issues, so healthcare organizations might need to consider hiring external security experts to assess their systems and help improve them.










