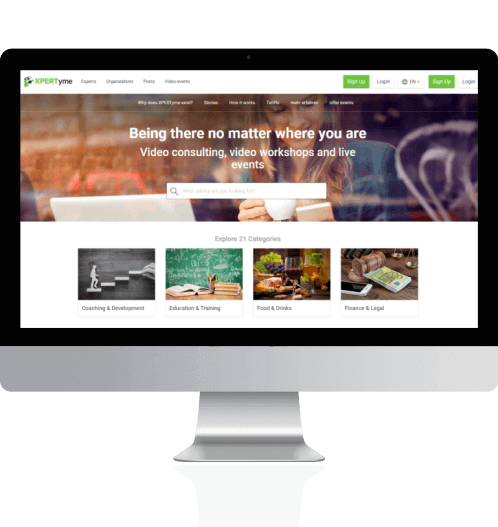
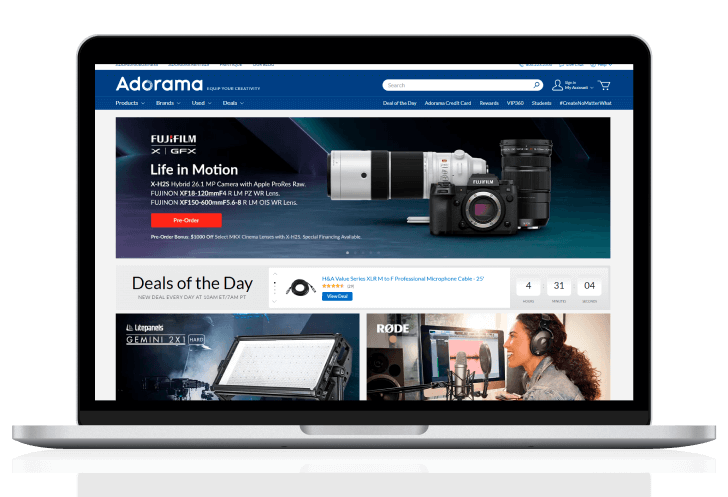
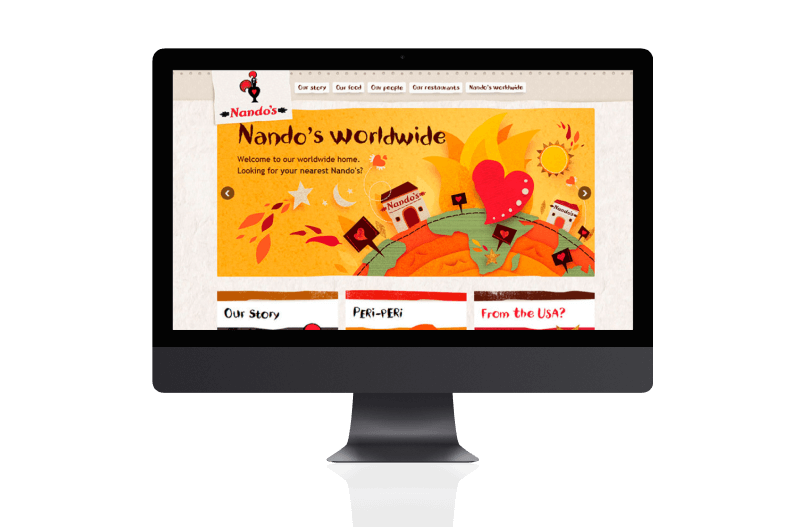
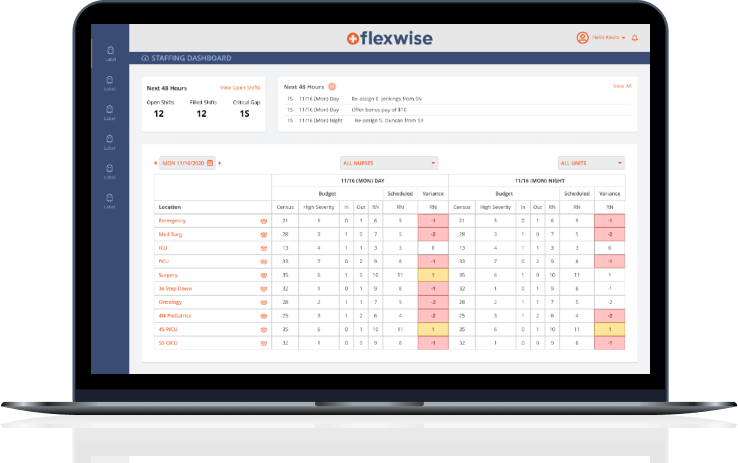
Custom software development
IT Craft’s custom software development services include a wide range of skills and competencies to meet your technical challenges flexibly.
We find the unique combination of outsourcing experts you need to achieve high-quality growth and long-term adaptability in your specific environment.
Schedule a short introduction call with our experts.
Why Do You Need Custom Software Development Solutions?
Custom software is the key when your business success relies on efficient internal processes. It enables you to:
Rapid Change Management
You can adapt available functionality and add new features quickly when you envisage enhancements in your workflow.
Cost-Effectiveness
Custom software is cost-effective in the long run, while you pay only for features you use.
Sustainable Transformations
Maintaining implementation rigor is easier, especially when you order custom software development outsourcing by experts who know how to keep you on track.
Enhanced Security
Your company retains full control over its internal data and processes. Your software is built with specific security concerns in mind.
Our services
Download your Software outsourcing smart guide
Finding right outsourcing partner is crucial for your business success. We will explain how to get one.
Download now
Our Case Studies
Client success stories
Do you want to improve business efficiency?
Let’s bring your system to the next level with IT Craft’s uncompromised custom software development services.
Contact us
How we work
Our Recognitions
Our custom software development company has amassed wide experience successfully launching software across various industries—globally.
Over 20% of IT Craft's engineers have been working in the industry for 15 – 20 years, covering critical current and old development technologies.
Many of our clients not only choose to stay with us but also provide references and recommend our services to others.
Why Choose Custom Software Development Company IT Craft?
Unique approach to each new project
IT Craft developers treat each new project with the beginner’s mind to provide the best solution to the client needs.
Focus on value
We prioritize the scope of custom software development services based on the provided value. If you change your strategy, we refocus on what is now important.
Fast-paced deliveries
Our teams work in two-week Sprints. You test the results immediately. Using acquired best practices and know-how enables us to deliver up to 30% faster.
Cost-savvy development processes
The IT Craft teams have built internal frameworks, which let us boost development and save up to 50% of the development budget in the initial stages.
Industries Where We Are Experts in Mobile App Development
Custom mobile app development firm IT Craft delivers solutions across 20+ industries and counting.
Our engineers dive deeply into your industry's specifics to help you eliminate pitfalls, launch effectively, adapt to user habits, comply with regulations, and more. With our accumulated expertise, you move forward faster.
-
On-demand app development
-
Logistics
-
Fantasy Sports & Gaming
-
Food delivery app development
-
iBeacon app development
-
IoT app development
questions from our clients
What is custom software development services?
Custom software development services focus on building and maintaining solutions that meet special business needs.
Usually, a custom software development firm helps you produce features that are unavailable in off-the-shelf software or cost too high to implement.
Custom software development services include:
- Discovery
- Software architecture
- UX/UI design
- Code development
- Integrations
- QA and testing
- Software administration and updates
- Scaling and optimization
How much does custom software development cost?
Costs of custom software development services vary from $5,000 for a simple prototype to $500,000 and higher for a large, fully featured ERP system.
Check more in: “Enterprise Software Development Explained: Benefits, Processes, and Best Practices to Keep a Close Eye on in 2025.”
Why choose custom software development?
Here are the main reasons to choose custom software development services:
- Companies get specific functionality that is tailored to unique needs and challenges.
- They are better prepared for the future and can adapt to a rapidly changing environment.
- There is a high level of control over security and data protection activities.
A custom software development agency can be a company’s helping hand in optimizing development workflow and delivering required features.
What cooperation model is better for custom development?
Time and material is more beneficial for custom software development services because it lets developers better handle unforeseen challenges.
Still, fixed-priced cooperation is also possible upon a comprehensive project discovery when the project scope remains unchanged.