DevSecOps is vital in today’s digital landscape, especially considering the alarming statistics around cyber threats. In 2023, the cybersecurity landscape was marked by significant challenges and trends:
- CrowdStrike’s 2023 Global Threat Report highlights a 95% increase in cloud exploitation and a 112% increase in access broker ads on the dark web, underscoring the evolving nature of cyber threats.
- The global cost of online crime is projected to reach $10.5 trillion annually by 2025, highlighting the financial implications of these threats.
This guide is essential for developers, security experts, and operations teams. It offers insights for implementing DevSecOps to ensure more secure and efficient software development.
1 Understanding DevSecOps: An Overview
DevSecOps stands at the forefront of modern software development, offering a robust and integrated approach where security is no longer a separate phase but a fundamental aspect of the entire development process.
This methodology merges the speed and agility of DevOps with the meticulousness of protection protocols, creating a harmonious environment where code is developed, tested, and secured simultaneously.
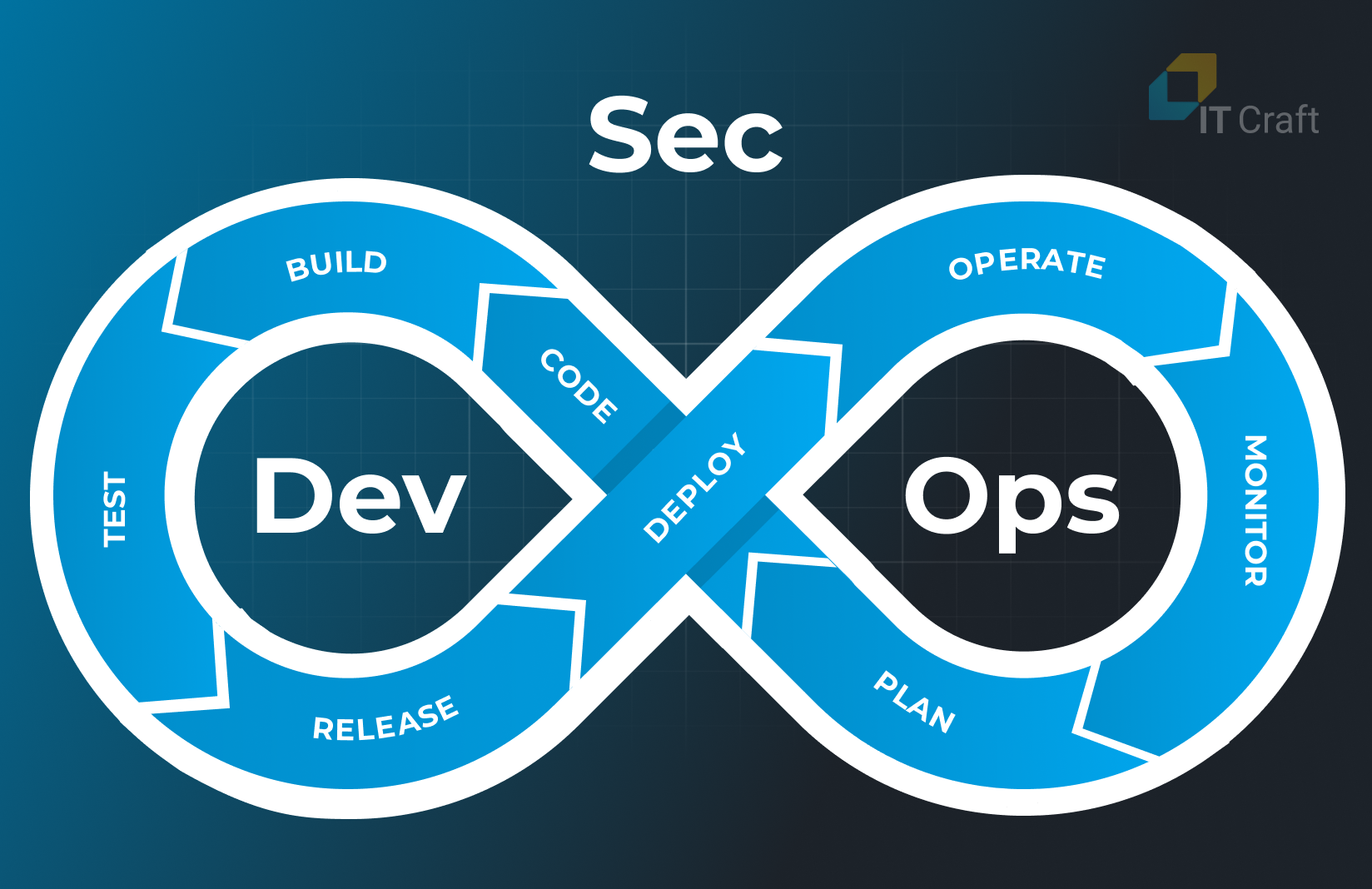
Key aspects of DevSecOps include:
- Integration of Security in Development
Unlike traditional models where protecting the software product is a final step, DevSecOps integrates security measures into every phase of the software lifecycle, making it a fundamental component.
- Collaboration Across Teams
DevSecOps fosters collaboration among development, safety, and operations teams, leading to faster and more secure software development.
- Automation of Security Protocols
DevSecOps minimizes human error and expedites secure software delivery by automating data protection processes.
- Proactive Vulnerability Identification
Security is addressed early in the development cycle, allowing for the early detection and resolution of potential issues, reducing risks and post-development costs.
- Cultural Shift
DevSecOps necessitates a mindset change for developers and data protection professionals, advocating for a more integrated and collaborative working environment.
2 DevSecOps and DevOps: Unraveling the Key Differences
Understanding the distinction between DevSecOps and DevOps is crucial for modern software development practices.
While both approaches aim to streamline and optimize the software development lifecycle, they differ significantly in their focus and methodology.
DevOps: The Foundation
A blend of development and operations, DevOps emphasizes collaboration between software developers and IT operations.
DevOps aims to shorten the development lifecycle, fostering a high degree of automation and continuous delivery to improve software quality and responsiveness to feedback.
DevSecOps: Integrating Security
DevSecOps extends DevOps by integrating security into every stage of the development process. It’s not just a practice but a cultural shift that incorporates security as a shared responsibility within the DevOps model.
DevSecOps emphasizes:
- Early Integration of Security
It incorporates protective measures and evaluations at the beginning of the development process rather than treating them as an afterthought.
- Ongoing Security
These are tools for protecting the software development and deployment processes within the continuous integration and continuous delivery (CI/CD) pipeline, ensuring constant vigilance against security vulnerabilities, compliance breaches, and quality issues.
- Collective Responsibility for Security
The duty of ensuring it is shared across all teams — development, operations, and beyond — making it a part of everyone’s daily tasks.
- Anticipatory Risk Management
DevSecOps actively seeks out and addresses potential safety concerns, aiming to minimize vulnerabilities in the final software product.
Key Differences between DevSecOps and DevOps
The main differences you should know are the following:
- Focus
While DevOps focuses on unifying software development and operations, DevSecOps brings in an additional layer of security right from the start of development.
- Security Integration
In DevOps, security might still be a separate final step. In contrast, DevSecOps embeds security practices and tools throughout the development lifecycle.
- Cultural Shift
DevSecOps requires a broader cultural shift where every team member becomes accountable for security, compared to DevOps, which focuses on collaboration between developers and IT operations.
- Outcome
Integrating safety in DevSecOps aims to produce software rapidly and ensure it is inherently secure, reducing the risks and costs associated with post-development fixes.
Ready to choose between DevSecOps and DevOps for your project?
Embrace a secure development approach with our expert insights!
Contact Us
Implementing DevSecOps in your organization brings many advantages backed by compelling statistics that underscore its importance in modern software development.
- Enhanced Security Posture
By integrating security practices from the start of the development cycle, DevSecOps significantly reduces vulnerabilities.
A Gartner report suggests that 75% of security failures result from inadequate application risk management, not the security infrastructure. DevSecOps directly addresses this by making security a core part of development.
- Cost-Effective Development
Fixing issues in the development phase is exponentially cheaper than addressing them post-release.
The IBM Cost of a Data Breach Report 2023 indicates the global average cost of a data breach in 2023 was $4.45 million, marking a 15% increase over three years. Early detection and mitigation of security issues can significantly reduce these costs.
- Improved Compliance
With rising concerns over data privacy and regulations like the GDPR, implementing DevSecOps ensures compliance is integrated into the software development process.
This proactive approach reduces the risk of non-compliance penalties, which can be substantial.
- Customer Trust and Satisfaction
A secure product is trustworthy. By ensuring robust security measures, DevSecOps builds customer trust and satisfaction — key elements for business success in today’s technology-driven market.
4 How Does DevSecOps Work?
DevSecOps works by embedding security measures and practices throughout the software development lifecycle.
This integration is not just about adding new tools but involves a cultural shift in how security is perceived and handled within development and operations teams.
Here’s how DevSecOps functions:
- Early Integration of Security
In DevSecOps, security is considered right from the planning stage. This early integration helps identify potential security issues before they become major problems.
- Collaboration Across Teams
DevSecOps fosters a culture where developers, operations, and safety teams work closely together. This collaboration ensures that security considerations are seamlessly integrated into the development process.
- Automated Security Testing
Automation is a key component of DevSecOps. Security tests are automated and integrated into the continuous integration and continuous deployment (CI/CD) pipeline.
- Continuous Monitoring and Feedback
DevSecOps monitors deployed software for security threats. Feedback from this monitoring is used to make improvements, ensuring ongoing protection against new vulnerabilities.
- Shared Responsibility for Security
Data protection is not the sole responsibility of a dedicated team but is a shared concern across all teams involved in the software development process. This shared responsibility ensures that security is a priority at every stage of development.
- Incident Management and Response
DevSecOps includes robust incident management and response strategies. There are predefined procedures for quick and effective responses during a security breach.
- Training and Awareness
Regular training and awareness programs keep all team members updated on the latest data protection practices and threats. This helps in building a security-conscious culture within the organization.
5 Exploring DevSecOps Tools: What Are They?
DevSecOps tools are advanced software solutions designed to weave safety measures into the DevOps process seamlessly. These applications enable automated vulnerability checks and constant system surveillance, and they incorporate protective measures as a core aspect of the software development cycle.
Key categories of DevSecOps tools:
- Code analysis tools
Automatically analyze source code for security vulnerabilities. They are integrated into the CI/CD pipeline and can identify potential security issues early in development.
- Container security tools
With the growing use of containerization, these tools focus on securing containerized applications. They manage container configurations, scan for vulnerabilities, and enforce security policies.
- Compliance monitoring tools
Ensure that software development complies with industry standards and regulations. They continuously monitor and report compliance statuses, helping teams promptly address security gaps.
- Threat intelligence tools
Provide real-time insights into emerging threats. Keeping development teams informed about the latest security risks enables proactive measures to safeguard applications.
- Incident management tools
These tools facilitate quick response and recovery during a security breach. They help identify the cause of the breach, contain the threat, and prevent future incidents.
- Identity and access management (IAM) Tools
Control who can access certain software parts, ensuring that only authorized personnel can access sensitive data.
- Security orchestration and automation Tools
Automate repetitive security-related tasks, streamline workflows, and improve collaboration between development, safety, and operations teams.
6 Optimizing Development Security: DevSecOps Best Practices
Integrating DevSecOps into the software development lifecycle involves more than just technical adjustments; it requires a holistic approach that combines strategic practices with cultural changes. Early integration of security involves:
- Automation of Security Processes
- Continuous Monitoring and Feedback
- Shift Left Approach
- Compliance Management
- Cultural Shift in the Organization
- Training and Awareness
- Tool Integration
- Incident Response Planning
- Iterative Improvement
These best practices are essential for embedding security seamlessly into every stage of development.

Early Integration of Security
The key to DevSecOps is starting with a security-centric approach.
- Embed Security Early
Incorporate security protocols from the planning stage.
- Proactive Risk Management
Identify and address risks at the onset to prevent major issues.
- Cultivate a Security-First Culture
Ensure all team members prioritize data security.
Automation of Security Processes
Automation plays a crucial role in integrating protection into DevOps.
- Automated Security Checks
Implement tools for continuous integration and delivery (CI/CD) that automatically test and secure each step of the development process.
- Efficiency and Reliability
Automation enhances security while streamlining development processes.
Continuous Monitoring and Feedback
Constant vigilance is essential in the ever-evolving software development field.
- Ongoing Security Assessments
Implement real-time monitoring tools and processes.
- Adaptive Security Strategies
Use feedback to refine safety measures dynamically.
Shift Left Approach
The shift left approach concerns early security integration in the development cycle.
- Early Testing
Incorporates security testing early in the development process.
- Timely Issue Resolution
Detects and addresses security issues sooner for more effective solutions.
Compliance Management
Compliance with industry standards is a key component of DevSecOps.
- Regular Audits and Updates
Stay aligned with the latest compliance requirements.
- Reinforce Software Security
Ensure development practices meet legal and security standards.
By blending these practices with a culture that values protection at every step, organizations can effectively implement DevSecOps. This approach not only fortifies the security of software products but enhances the overall efficiency and responsiveness of the development process.
7 The Art of Implementing DevSecOps in Your Organization
Implementing DevSecOps within an organization is an art that requires a balanced approach, blending technical know-how with a cultural shift toward security. This process involves several key steps:
- Assessment and Planning
- Begin with a thorough assessment of your current development and security processes.
- Identify areas where security can be integrated more deeply into the development lifecycle.
- Cultural Shift
- Cultivate a culture where security is everyone’s responsibility, not just the security team’s.
- Encourage open communication and collaboration between development, operations, and safety teams.
- Training and Awareness
- Conduct regular training sessions to keep all team members up to date on the latest security practices and threats.
- Promote a continuous learning environment where team members can share knowledge and insights.
- Tool Integration
- Choose and integrate tools that align with your DevSecOps goals.
- Ensure these tools are conducive to automating security checks and streamlining workflows.
- Automation and Continuous Integration
- Implement automation in as many safety processes as possible.
- Integrate safety checks into your CI/CD pipeline to ensure continuous assessment.
- Continuous Monitoring and Feedback
- Set up systems for continuous monitoring of safety postures.
- Use feedback from these systems to improve security and development processes.
- Incident Response Plan
- Develop a comprehensive incident response plan for potential safety breaches.
- Regularly test and update this plan to ensure its effectiveness.
- Iterative Improvement
- Adopt an iterative approach to implementing DevSecOps, starting with small, manageable changes.
- Continuously review and improve your DevSecOps practices.
By following these steps, organizations can smoothly transition to a DevSecOps approach. This transition enhances the security of the software being developed and fosters a more efficient and collaborative work environment.
Deciding on DevSecOps vs DevOps?
Discover which fits your needs with our expert guidance.
Get insights now
8 How Does Penetration Testing Work in DevSecOps?
In the context of DevSecOps, penetration testing plays a crucial role as a proactive security measure. It involves simulating cyber attacks on software systems to identify and fix vulnerabilities before they can be exploited in real-world scenarios.
Here’s how penetration testing integrates into the DevSecOps process:
- Strategic Planning
- Penetration tests in DevSecOps are strategically planned to align with the development lifecycle.
- Testing is scheduled regularly and in sync with major release cycles.
- Collaborative Effort
- Unlike traditional models, DevSecOps developers, operations teams, and security experts collaborate on penetration testing.
- This collaboration ensures a comprehensive understanding of the system from multiple perspectives.
- Automated and Manual Testing
- Unlike traditional models, DevSecOps developers, operations teams, and security experts collaborate on penetration testing.
- This collaboration ensures a comprehensive understanding of the system from multiple perspectives.
- Continuous Integration
- Automation tools are employed for continuous penetration testing, identifying vulnerabilities early in development.
- Manual testing complements automated tests, targeting complex, high-risk areas that require expert analysis.
- Analysis and Feedback
- Penetration testing tools and methods are integrated into the CI/CD pipeline.
- This integration allows for continuous, automated security assessments as part of the development process.
- Actionable Remediation
- Results from penetration tests are analyzed to identify security weaknesses and potential attack vectors.
- Feedback from this analysis is used to improve security measures and inform future development.
- Once vulnerabilities are identified, actionable steps are taken to remediate them.
- Developers work closely with security teams to patch vulnerabilities, enhancing the application’s overall security.
- Documentation and Compliance
- Results and actions taken are meticulously documented for compliance purposes and future reference.
- Documentation also aids in assessing the effectiveness of security strategies over time.
Incorporating penetration testing into the DevSecOps framework ensures a robust and proactive approach to security. It enables organizations to effectively identify and address vulnerabilities, significantly reducing the risk of security breaches in their software solutions.
9 IT Craft's Expertise
Flexwise DevSecOps Transformation: Enhancing Healthcare Systems
Since 2018, Flexwise has been advancing its healthcare workforce management platform by transitioning to cloud infrastructure.
The five-member team focused on improving workload efficiency and stability. They addressed challenges such as outdated software, slow market integration, and compliance with healthcare regulations, particularly for secure data handling.
Key Achievements:
- Raised $6M in funding
- Reduced scaling costs by up to 35%
- Attained 99.9% security coverage
Transformation Impact:
- Cloud Migration: Transitioned to a modern, flexible, and secure cloud solution.
- Enhanced Agility: Automated management tools streamlined operations, improving deployment speed and efficiency.
- Robust Security: High-level protection was achieved using state-of-the-art technology complying with HIPAA requirements.

DevOps Consulting and Transformation for MyPlace Connect
Enhancing Infrastructure for Market Growth.
Since 2018, MyPlace Connect has focused on upgrading its infrastructure to attract and retain users, with a three-member team specializing in DevOps and IT Consulting for the marketing industry.
Our DevOps team led the audit and designed a migration plan focusing on software stability, choosing Kubernetes for its efficient cloud integration and smart scaling capabilities.
Results Achieved:
- Customer Growth: 30% increase
- Reduced Scaling Cost: Up to 50%
- Migration to EKS (Amazon Elastic Kubernetes Service) facilitated stable, cost-effective user activity peaks and multi-layered, secure infrastructure.
Business Benefits:
- Project Control: Centralized management with simplified changes
- Cost Efficiency: Pay-for-what-you-use resource management
- Reliability: Easy tracking and rollback with GitOps
Security: Reduced human error and improved external attack surface management (EASM)

FAQs
The four key components of DevSecOps are:
- Integration: Seamless blending of security practices into the DevOps process
- Automation: Using automated tools for continuous security testing and monitoring
- Collaboration: Fostering a culture where development, operations, and security teams work together
- Continuous Improvement: Regularly assessing and enhancing security measures in the development lifecycle
To start with DevSecOps:
- Assess Your Current Setup: Evaluate your existing development and security processes
- Educate Your Team: Provide training on DevSecOps principles and practices
- Select the Right Tools: Choose tools that facilitate automation and integrate security
- Implement Gradually: Start integrating security practices into your existing DevOps pipeline step by step.
The DevSecOps method integrates security practices directly into software development and deployment. It emphasizes automation, continuous security assessment, and collaboration across development, operations, and security teams, aiming to build, test, and release software rapidly and securely.
Coding is only sometimes a direct requirement for DevSecOps, but understanding the basics of coding can be beneficial. It helps you to automate security processes, understand software vulnerabilities, and communicate effectively with development teams. However, the focus of DevSecOps is more on integrating and automating security processes rather than on coding itself.


